Monday, October 1, 2018
#Cyberaware Week 1 Stop Think Connect
National Cybersecurity Awareness Month #CyberAware is a collaborative effort between industry and government.
To get you off to a good start, here is a toolkit from Homeland Security. It's good because it has tips for different audiences and for different topics. Something for everyone!
Take advantage of the toolkit!
and
Stay Safe!
Sunday, September 30, 2018
Changing Your Facebook Password--The Facebook Breach
On Tuesday we learned that Facebook had suffered a breach that affected about 50 million users, people who used the "View as" feature on the platform. Actually, Facebook logged 90 million users out of their Facebook page 'out of an abundance of caution.' For more detail, read this post from TechCrunch.
A critical thing to understand is that this potential theft of a user's login data affects all sites the user has logged into using her Facebook user name and password. In the interest of protecting yourself, set up a separate password for each site--DO NOT USE FACEBOOK or any other platform's login data. Too much trouble? Read my post on using a password manager. A password manager makes that easy to do and gives additional benefits.
I rarely use Facebook but I've had an account for years, so I decided to change my password, partly at the prompting of my password manager. Here are things I learned along the way.

The first time I signed into my password manager, which is pinned to my Start menu, I saw the alert on the left--a quick warning about the breach. A couple of days later I got the more specific alert on the right telling my that 49 of my accounts had been compromised!
Does that mean that 49 of my accounts had been breached? No, it means that 49 of my accounts used elements of my Facebook password. I admitted to lazy password habits in the password manager post and I haven't bothered to change many of them. This time I decided I would at least change my Facebook and bank passwords.
Changing my Facebook password was easy. Using my password manager, a 'create a secure password' box pops up each time I change a password. It creates a 12-digit password composed of upper case and lower case letters, numbers and special characters. It is virtually unhackable and equally impossible to remember! Your password manager will use it to sign you in automatically, so you don't need to remember it--thank goodness!
Ok, so now I have a safe Facebook password--on to my bank. I followed the same process and the site refused my password. I didn't understand, so I tried again with the same result (yes, I know the popular definition of insanity!). The second time I read carefully and understood that it was rejecting the special characters in the strong password created by the password manager.
Then I actually read the rules of the bank's passwords. The rules did not require a combination of upper case and lower case letters and it did not require special characters, both requirements of many sites. I created a new password using its rules. I'm confident that it is not as strong but it's so silly that I wonder if a human hacker could crack it. But what about a sophisticated tech hack?
I used their contact form and asked to speak to a rep knowledgeable about their password system. If I have an interesting response, I'll write about it at a future date.
I'll repeat the advice that is all over the web and add two more that aren't repeated as often but are equally important.
Related Updates!
Facebook use of 2-factor authentication, mobile numbers
A critical thing to understand is that this potential theft of a user's login data affects all sites the user has logged into using her Facebook user name and password. In the interest of protecting yourself, set up a separate password for each site--DO NOT USE FACEBOOK or any other platform's login data. Too much trouble? Read my post on using a password manager. A password manager makes that easy to do and gives additional benefits.
Changing My Facebook Password
I rarely use Facebook but I've had an account for years, so I decided to change my password, partly at the prompting of my password manager. Here are things I learned along the way.

The first time I signed into my password manager, which is pinned to my Start menu, I saw the alert on the left--a quick warning about the breach. A couple of days later I got the more specific alert on the right telling my that 49 of my accounts had been compromised!
Does that mean that 49 of my accounts had been breached? No, it means that 49 of my accounts used elements of my Facebook password. I admitted to lazy password habits in the password manager post and I haven't bothered to change many of them. This time I decided I would at least change my Facebook and bank passwords.
Changing my Facebook password was easy. Using my password manager, a 'create a secure password' box pops up each time I change a password. It creates a 12-digit password composed of upper case and lower case letters, numbers and special characters. It is virtually unhackable and equally impossible to remember! Your password manager will use it to sign you in automatically, so you don't need to remember it--thank goodness!
Changing My Bank Password
Ok, so now I have a safe Facebook password--on to my bank. I followed the same process and the site refused my password. I didn't understand, so I tried again with the same result (yes, I know the popular definition of insanity!). The second time I read carefully and understood that it was rejecting the special characters in the strong password created by the password manager.
Then I actually read the rules of the bank's passwords. The rules did not require a combination of upper case and lower case letters and it did not require special characters, both requirements of many sites. I created a new password using its rules. I'm confident that it is not as strong but it's so silly that I wonder if a human hacker could crack it. But what about a sophisticated tech hack?
I used their contact form and asked to speak to a rep knowledgeable about their password system. If I have an interesting response, I'll write about it at a future date.
The Take-Aways
I'll repeat the advice that is all over the web and add two more that aren't repeated as often but are equally important.
- Change Your Facebook password.
- Change the password on every site you have, or even think you have, logged into with Facebook.
- Use a unique password for each site with which you set up an account. Never log onto a site using your credentials from another platform.
Related Updates!
Facebook use of 2-factor authentication, mobile numbers
Friday, September 28, 2018
National Cybersecurity Awareness Month
I'll be publishing as often as I can during October.
Look for the #CyberAware wherever you go in October!
Tuesday, September 18, 2018
Getting The Most Out Of Search
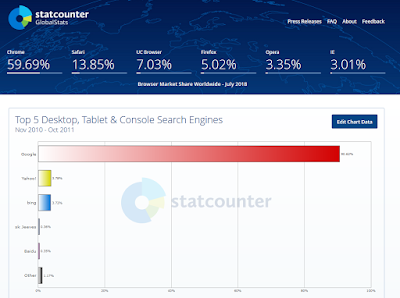
In this post I’m going to focus exclusively on Google. The chart explains the first reason. First, over 90% of searches take place on Google. Second, all the general search engines work in essentially the same way so if you prefer another one, these tips will work also. There are also specialized search engines like Google Books. The USA.gov search engine link on the page has changed and it looks as if it could be quite useful.
Click the little magnifying glass on the search bar to see which search engines are available and which one is being used as the default. The default search engine is set from inside the browser, so if you want to change it you can search browser options or just search ‘change default search engine [browser name].’ That’s your first tip. Make searches as specific as possible, then you will get the specific information you are looking for. I find it bit disheartening that I often find information more easily by doing a web-wide Google search than I do by searching for it on the website where I know it should be.
How Do Search Engines Work?
Search engines ‘crawl’ the web looking for content. Then they ‘index’ that content--basically put it in a big database. Then they decide how to show it on the search results pages. They could just do something like ‘most recent’ but that wouldn’t guarantee useful results to searchers. After all, that’s what keeps people coming back—the fact that they get results that help them in their daily lives.
So the search engines use algorithms (formulae) to ‘rank’ content. Google is said to use about 200 different pieces of information to rank each item of content. No, Google doesn’t say exactly how many. Nor does it tell us what any of them are. Why? Because they don’t want web publishers (from me to the big guys) gaming the system. As it is, a lot of skilled search engine marketers spent their working days reverse-engineering the system to see what factors affect ranking and how. Then, thankfully, they tell the rest of us. So we know a lot, but most of it doesn't come from the search engine itself. Google has placed emphasis in recent years on ‘quality content’ but they don’t tell us exactly how they judge it!
How Should Users Navigate the Huge Amount of Content on the Web?
Fortunately, there is only one thing the average searcher absolutely has to understand. Keywords are at the center of how items are ranked and therefore how individual users find content. Look at the bottom of this post. You will see Labels. Those are keywords I have selected on the basis of what I believe people will be looking for relative to this particular blog post. If I guess right, people are more likely to find the post. And if more people find it, Google will rank it higher in its search results. It’s all about what people find useful, and that’s as it should be.
Three other things that are useful are illustrated in this search results page for ‘fried chicken recipe.’ The first result comes in the form of a ‘snippet,’ a summary of a good answer with a link to the full post. Look at how many keywords are showing. The next result is an ‘answer box,’ which is based on questions people most often ask about this subject. Google then
supplies what it considers the one best answer to that question. The answer box is followed by other results, in rank order. Hint: if you remember your grandmother talking about buttermilk when she talked about her fried chicken, search ‘buttermilk fried chicken recipe.’ If you are looking for specific information, make a specific query—just makes sense!
The question issue is important. A couple of years ago Google realized that people were asking questions of their virtual assistants to trigger search queries. It has reconfigured some aspects of how it presents results in response. That means a searcher often gets a good answer when the search is posed as a conversational question. Neither capitalization nor question mark required!
So is the toolbar directly underneath the search box. By default it is set on All. You might enjoy the Shopping tool. And look on More to see additional options. The one that I find really useful is News. It contains most recent--as opposed to most visited--posts. Sometimes that is exactly what the searcher wants!
Related to that is the recency of the post, which we know is one of Google's ranking factors. If you are looking for something like the fried chicken your grandmother used to make, recency doesn’t matter to you. If you are looking for the latest developments in breaking news, it is critical. If you are looking for something about the internet, I suggest you ignore anything older than a year and confirm any recent information from at least one other source. Make it easy and search for ‘xxx2018.’ Remember to be specific and remember that the internet changes daily!
The searcher should also look at the credibility of the site that posted the content. Some of them you will know; many of them you will not. Just because the site is not familiar does not mean it is not good (or is not bad, for that matter). I recommend two steps, always:
• First, look at the About page on the site. Simply read it to see whether it is company you want to keep.
• Second, follow the rule of journalism. Don’t accept the word of just one site for factual information. Keep looking for a fried chicken recipe until you find one that sounds like your grandmother’s—that’s one thing. But if you are looking for, say, medical information, you don’t want to accept the first content you come to, even if the site is known and credible. Keep on looking. My recommendation on something really important is to keep searching until you are reading nothing new, nothing that you didn’t already know. If you want a rule of thumb, three is usually good if they all agree. Personally I like the ‘nothing new’ rule of thumb.
Here are some other specifics that should make searching easier:
• Use long and specific search queries
• Capitalization does not matter, either way
• Use quotation marks around a phrase to get the exact words, not all related words
• Common and connector words (the, a, etc.) are usually ignored. The exception is when they are inside quotation marks.
• Use the AutoComplete function directly below the search box. It ensures that the spelling is correct as well as giving you common searches on the subject. It is also useful to suggest different terms and phrases to search.
• Use the ‘related results’ at the bottom of the search results page for different approaches to finding the information. Related searches are also seen in the answer box.
• When looking for a product or service, include the word ‘best.’ The search will return a lot of rating and ranking articles (remember to pay attention to the date), which give useful, often comparative, data.
Next Steps
This is just an introduction. It may be enough to make your daily internet life more productive. However, if you want to go further, here are some suggestions.
• Here is what's essentially a search exercise that guides you through several search tasks on several search engines. It is very instructive but I can’t find how recent it is. So if you are sure you have followed the instruction correctly and it doesn’t work, go on to the next item. Remember, the internet changes daily!
• Here’s one good article (posted in 2018) on how to do good Google searches. Why don’t you read it and then use your new-found search skills to find out more about issues you find important and useful?
Stay safe!
Update
A couple of days ago I ran across a couple of things that interested me, but when I searched for them I found neither had actually happened yet. One was a new news site that will get considerable notice when it starts publishing around the first of next year, so I just relied on seeing that on one of my news feeds. The other was somewhat local. I wanted to know about it in a timely fashion, so I set up a Google Alert. When you create a Google Alert, you are asked how often you want notices, so your inbox is not going to get flooded with emails. Besides, they are easy to set up and take down, so they can be used and closed freely. I encourage you to use them for issues you want to easily track!
Related Links
New Google tools help organize, keep track of searches
Tuesday, August 21, 2018
Do Privacy Laws Protect Internet Users?
There’s one easy answer to that. If privacy laws were sufficient to protect users, I wouldn’t need to write this blog! Users should know the ways in which laws try to protect them and how to take advantage of protections offered. Even then, it’s always “User Beware” on the internet.
Privacy laws, in the US and other countries, are designed to protect user data. Keep in mind that is important but not quite the same as protecting users while they travel the net. Privacy laws are focused on the ways in which businesses collect, store and use their customers’ data. Businesses necessarily require data to complete transactions. They should only store that data beyond the transaction with user permission. They should destroy data for which there is no permission after a ‘reasonable’ time.
Both of those principles are often violated. In 2000 the credit card numbers of Bill Gates and thousands of other well-known people were stolen from registration data at the World Economic Forum in Davos, Switzerland. Unbelievably, the same thing happened on a smaller scale in 2008, and they got Bill Gates’ number again. The hackers are not plucking these numbers out of the ether. They are accessing them after they had been stored in a commercial database. In the 2000 hack data had unnecessarily been stored long after the conference was over. In 2018 it looks as if conference protesters were banned from the area and went off and hacked its records just ‘to show them’. Either way, it was embarrassing.
This world map gives an overview of the strength of data protection laws. The link takes you to the interactive version. US is shown as barely adequate while the EU is in a category of its own. More about the EU in a moment.
Many ratings give Iceland the top rating for the strictness of its data protection laws. The Scandinavian countries are mentioned frequently. Some tech experts argue that makes those countries strong candidates for locating firms that specialize in cyber security. The fact is that the large companies are global, which forces them to comply with the strongest laws. Users might be better off looking at where a company does not operate—does that mean the company is avoiding strong laws? The case in point at the moment is the General Data Protection Regulation of the European Union which went into effect in May of this year. Among other things, it has caused some US companies to block users from EU companies because they are not complying with the regulations and do not want to face stiff fines. I wrote a post for marketers last fall. This infographic summarizes the salient points.
The GDPR requires that all companies doing business in an EU country abide by the regulations, which have the force of law. Large fines can be imposed on firms that do not comply. Here is what consumers can expect in terms of protection under the GDPR:
• To be informed about how and why data is being collected by means of privacy statements
• To have access to their data and to information about how it is being processed
• To have incorrect or incomplete data corrected
• To have data erased when there is no compelling reason for further processing. This is often referred to as “forgetting a data subject.”
• To restrict the processing of personal data
• To provide for transfer of data from one IT environment to another (data portability)
• To object to certain types of data processing
• To be protected against harm from automated data processing that is not subject to human intervention.
The term ‘processing’ appears frequently. What does it mean? Basically, it means any operation performed on the personal data of subjects, from collection to storage to statistical manipulation to use in a communications activity. Here is a definition from a German consulting company that specializes in the GDPR:
‘processing’ means any operation or set of operations which is performed on personal data or on sets of personal data, whether or not by automated means, such as collection, recording, organisation, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction;
In other words, anything done with or to the data.
Consumers should take the protections listed above seriously. If they make a data-related request and it is not honored, that’s a big signal that the company is not meeting its legal obligations. In the US the Federal Trade Commission is the agency most directly concerned with data security and privacy issues. The FTC is concerned with all types of scams and rip-offs and they have a page on which consumers can voice concerns about privacy. That type of concern goes under their Identity Theft heading.
There is a visible way consumers can be aware that a website is complying with strict data protection policies. The page below contains a privacy notice I found while researching this post. As many you see these days, it warns about the use of cookies, those snippets of code that track users on the web.
• At the lowest level of acceptable permission a privacy notice just says something like “continuing to use this site will constitute acceptance of our cookie policy.” Ok, the user has been warned.
• A higher level is to require the user to click something like an Accept box before continuing to use the site. The user has done something proactive, suggesting at least a minimal level of attention.
• The graphic below has a link to the website’s settings, encouraging the user to actively manage the access and use of personal data. That’s a good, transparent thing to do and consumers should take advantage of it.
The other type of notice frequently seen these days is one that says, “We’d like to send you notifications.” The user must give an affirmative reply to start the notifications but usually has to check the negative just to get rid of the box.
The laws are trying to offer protection, but it is hard to get out in front of the bad actor who always seem to have a new scheme up their digital sleeves. Users need the help of government agencies that have enforcement powers, The agencies need the help of internet users who see suspicious activity or recognize lack of required protections.
It is a case of “See Something, Say Something,” although it’s true that the wheels of justice can grind very slowly. Businesses have a huge responsibility to use consumer data with respect and to zealously protect any stored data. Consumers have a responsibility to look out for their own data welfare and to help identify malicious sites or those simply derelict in their duty.
Stay safe!
What Do Privacy Laws Protect?
Privacy laws, in the US and other countries, are designed to protect user data. Keep in mind that is important but not quite the same as protecting users while they travel the net. Privacy laws are focused on the ways in which businesses collect, store and use their customers’ data. Businesses necessarily require data to complete transactions. They should only store that data beyond the transaction with user permission. They should destroy data for which there is no permission after a ‘reasonable’ time.
Both of those principles are often violated. In 2000 the credit card numbers of Bill Gates and thousands of other well-known people were stolen from registration data at the World Economic Forum in Davos, Switzerland. Unbelievably, the same thing happened on a smaller scale in 2008, and they got Bill Gates’ number again. The hackers are not plucking these numbers out of the ether. They are accessing them after they had been stored in a commercial database. In the 2000 hack data had unnecessarily been stored long after the conference was over. In 2018 it looks as if conference protesters were banned from the area and went off and hacked its records just ‘to show them’. Either way, it was embarrassing.
The Strongest Data Protection
 |
| https://www.cnil.fr/en/data-protection-around-the-world |
Many ratings give Iceland the top rating for the strictness of its data protection laws. The Scandinavian countries are mentioned frequently. Some tech experts argue that makes those countries strong candidates for locating firms that specialize in cyber security. The fact is that the large companies are global, which forces them to comply with the strongest laws. Users might be better off looking at where a company does not operate—does that mean the company is avoiding strong laws? The case in point at the moment is the General Data Protection Regulation of the European Union which went into effect in May of this year. Among other things, it has caused some US companies to block users from EU companies because they are not complying with the regulations and do not want to face stiff fines. I wrote a post for marketers last fall. This infographic summarizes the salient points.
What Businesses Must Do To Protect Customer Data
The GDPR requires that all companies doing business in an EU country abide by the regulations, which have the force of law. Large fines can be imposed on firms that do not comply. Here is what consumers can expect in terms of protection under the GDPR:
• To be informed about how and why data is being collected by means of privacy statements
• To have access to their data and to information about how it is being processed
• To have incorrect or incomplete data corrected
• To have data erased when there is no compelling reason for further processing. This is often referred to as “forgetting a data subject.”
• To restrict the processing of personal data
• To provide for transfer of data from one IT environment to another (data portability)
• To object to certain types of data processing
• To be protected against harm from automated data processing that is not subject to human intervention.
The term ‘processing’ appears frequently. What does it mean? Basically, it means any operation performed on the personal data of subjects, from collection to storage to statistical manipulation to use in a communications activity. Here is a definition from a German consulting company that specializes in the GDPR:
‘processing’ means any operation or set of operations which is performed on personal data or on sets of personal data, whether or not by automated means, such as collection, recording, organisation, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction;
In other words, anything done with or to the data.
How Do Consumers Know Their Data Is Being Protected?
Consumers should take the protections listed above seriously. If they make a data-related request and it is not honored, that’s a big signal that the company is not meeting its legal obligations. In the US the Federal Trade Commission is the agency most directly concerned with data security and privacy issues. The FTC is concerned with all types of scams and rip-offs and they have a page on which consumers can voice concerns about privacy. That type of concern goes under their Identity Theft heading.
• At the lowest level of acceptable permission a privacy notice just says something like “continuing to use this site will constitute acceptance of our cookie policy.” Ok, the user has been warned.
• A higher level is to require the user to click something like an Accept box before continuing to use the site. The user has done something proactive, suggesting at least a minimal level of attention.
• The graphic below has a link to the website’s settings, encouraging the user to actively manage the access and use of personal data. That’s a good, transparent thing to do and consumers should take advantage of it.
The other type of notice frequently seen these days is one that says, “We’d like to send you notifications.” The user must give an affirmative reply to start the notifications but usually has to check the negative just to get rid of the box.
Once Again, Do Privacy Laws Really Protect Users?
The laws are trying to offer protection, but it is hard to get out in front of the bad actor who always seem to have a new scheme up their digital sleeves. Users need the help of government agencies that have enforcement powers, The agencies need the help of internet users who see suspicious activity or recognize lack of required protections.
It is a case of “See Something, Say Something,” although it’s true that the wheels of justice can grind very slowly. Businesses have a huge responsibility to use consumer data with respect and to zealously protect any stored data. Consumers have a responsibility to look out for their own data welfare and to help identify malicious sites or those simply derelict in their duty.
Stay safe!
Thursday, August 9, 2018
Does Every Internet User Need a Password Manager?
The answer is a definite YES! A good password manager is second only to good security software for protecting your personal data—and it’s a close second. It not only protects passwords, it also adds great convenience to your digital life.
Of course it’s important to protect your passwords, but think about how many you have and the sheer magnitude of the task. Think about how hard it is to remember them. Think about where you have them written down. Think about how many times you’ve used a child’s birthday or a pet’s name as a password—and how easy that would be to guess. So security is reason number one.
Reason number two is convenience. Filling out, not just passwords, but all those online forms is a pain. A password manager can auto-fill those for you. More about that in a moment.
A password manager is usually a piece of software, although it can be a hardware device, usually something that looks like a flash drive. I’m going to assume software because that is what I’m familiar with and it seems the most common.
Any password manager shares the same basic characteristics. It stores passwords in an encrypted (coded) form in a secure vault and uses a master password to access the stored passwords. Beyond that, password managers can and do have many other useful features. I've been using Dashlane for several years, so I'm going to use that as an example of what is typical of the best ones.
This is a screenshot of one account on my mobile phone (a router that I no longer own) as an example of some of the things a password manager does. Notice that I have also covered my email address and password. The password is shown with the typical dots but notice (second line) that you can see it or copy it, which is very useful. My password isn't very good and I've reused it 30 times--just like most of us do.
As a result, the password has been compromised. Dashlane describes a password as being compromised when any account that uses the password has been hacked.
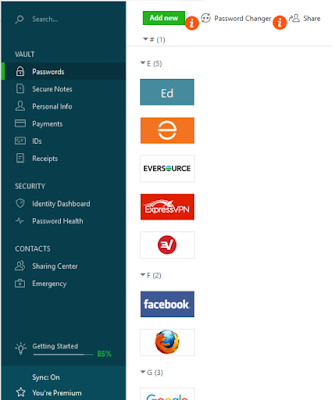
This information and more is shown on the screen on my laptop. I'm showing part of that below so you can see the menu, but I can't show more without revealing user names or blacking out a huge space. I also can't show a pulldown box that allows the user to change categories (about a dozen categories like business, news, and so forth allow passwords to be organized), deleted (like my closet, I should keep my passwords neater, deleting ones like the unusable Linksys), shared (with caution, although it is a useful feature) and enable auto-login, which I love but don't manage as actively as I should.
The graphic below lets you see what the same basic information looks like on a laptop screen. They are both usable, just different. I often prefer to use the mobile for a quick login to a site where I just want to check something.
The highly-rated password managers generally have the same basic features. What they do and do not have is explicitly stated on each site. The graphic is the Dashlane menu which has a number of features in addition to password management. The only other Vault feature I use is the Payments feature, although I could probably make good use of others.
My personal favorite, although it is not the most important from a security standpoint, is the autofilling of forms. I have to fill out a lot of forms because I often ask for information from websites. It’s so annoying to fill out a several-item form and try to submit it, only to discover that I have to go back and correct a typo. So the password manager makes my online life faster and more convenient and I love it for that. However, auto-fill is not an unmixed blessing: more about that in the Drawbacks section a little further on.
My second favorite thing is that the password manager can store credit card numbers and fetch numbers and billing info while the user is filling out an order. The password manager requires the master password in order to access a credit card, even though the user has already signed in, adding an extra level of security. It also adds to the ease of making purchases online, so you want to watch out for that! I try to be even safer by storing only one credit card online, that one being the one I use for everyday online purchases. Because I use it so much that credit card gets hacked from time to time and the bank immediately and graciously cancels it and issues a new one. That means the credit card in my password manager gets changed more frequently than my other credit cards and that’s good.
Most password managers offer free trial and the user should take advantage of it before deciding. Full-featured password managers are not free and their prices and scope of coverage (mostly additional devices) vary greatly, so be sure to comparison shop. I'm going to do a post on searching soon which will help a lot of people make online comparisons among different products.
The Security section also has useful information. The mobile capture shows an alert I received recently with the company name blacked out since I don't know the status. I immediately changed my password, using the Password Changer feature seen on the menu screen above. It gives strong passwords like bu9zibGWTCuc with a single command. All sites with sensitive data should use a strong, unhackable password like this and with the password manager a user doesn't have to make it up or remember it.

The Password Health screen again shows I don't really pay enough attention. Most of the passwords shown are not the result of a site that has been hacked, although some of them are. They are the result of using the same password as a site that has been hacked. That makes those passwords indirectly unsafe, I think. What I should do is first go through and delete the sites I never use and then change the passwords on the remaining sites. At the very least I should go through the list and see if there are any sensitive sites, primarily those with financial data, listed.
That suggests two more recommendations. First, be selective in setting up accounts on sites. If you do, give no more information than absolutely necessary. The best advice about storing credit card data is just don't do it. If your email address is taken in a hack, that's one thing. If your credit card is stolen, that's a big problem!
Second, think of your password manager account as a closet that needs to be kept clean. If you are prompted to save a password, be sure it is a new one. Otherwise you wind up with a dozen listings for the same account. There will inevitably be a few dups that should be removed manually to ensure that the right password is being fetched.
Like any other online operation, it is possible for password manager companies to be hacked. Security teams search the web for soft spots and all the major password managers have been called out at one time or another for a vulnerability that could open the door for hackers. These announcements are made public and the password manager firms appear to have been quick to work on the the flaws in their software, unlike many of their colleagues in other lines of work. Security experts themselves use password managers and point out that the benefits of using a password manager outweigh the risks.
Auto-filling is one of those risks. The process allows some hacking routines to syphon off email addresses. If you use it, as I do, be selective. As with everything else about this subject, the better protected the site itself is (a bank, for instance) the safer your data will be. If the site is questionable, the security of your data will be also.
When you decide to try out a password manager be sure it is pinned to your start menu. Then it will be ready when you need to use it--and I think you'll be using it a lot!
Consumer Reports has an open article on password managers that you should read before searching for one.
Stay safe!
Update 8/10/18
I forgot to mention that all the major browsers have a password manager. I checked mine on Firefox (Options => Privacy and Security). It has features like saving passwords and autofill. None of my research sites recommended using the password manager on a browser and some specifically recommended against it. That makes sense to me. Browsers are exposed to a lot of websites and that would increase the chance of picking up malware. Keeping passwords in the "locked vault" of a secure app seems to be better advice.
Of course it’s important to protect your passwords, but think about how many you have and the sheer magnitude of the task. Think about how hard it is to remember them. Think about where you have them written down. Think about how many times you’ve used a child’s birthday or a pet’s name as a password—and how easy that would be to guess. So security is reason number one.
Reason number two is convenience. Filling out, not just passwords, but all those online forms is a pain. A password manager can auto-fill those for you. More about that in a moment.
Just What Is a Password Manager?
A password manager is usually a piece of software, although it can be a hardware device, usually something that looks like a flash drive. I’m going to assume software because that is what I’m familiar with and it seems the most common.
Any password manager shares the same basic characteristics. It stores passwords in an encrypted (coded) form in a secure vault and uses a master password to access the stored passwords. Beyond that, password managers can and do have many other useful features. I've been using Dashlane for several years, so I'm going to use that as an example of what is typical of the best ones.
This is a screenshot of one account on my mobile phone (a router that I no longer own) as an example of some of the things a password manager does. Notice that I have also covered my email address and password. The password is shown with the typical dots but notice (second line) that you can see it or copy it, which is very useful. My password isn't very good and I've reused it 30 times--just like most of us do.
As a result, the password has been compromised. Dashlane describes a password as being compromised when any account that uses the password has been hacked.
This information and more is shown on the screen on my laptop. I'm showing part of that below so you can see the menu, but I can't show more without revealing user names or blacking out a huge space. I also can't show a pulldown box that allows the user to change categories (about a dozen categories like business, news, and so forth allow passwords to be organized), deleted (like my closet, I should keep my passwords neater, deleting ones like the unusable Linksys), shared (with caution, although it is a useful feature) and enable auto-login, which I love but don't manage as actively as I should.
The graphic below lets you see what the same basic information looks like on a laptop screen. They are both usable, just different. I often prefer to use the mobile for a quick login to a site where I just want to check something.
Features of Password Managers
The highly-rated password managers generally have the same basic features. What they do and do not have is explicitly stated on each site. The graphic is the Dashlane menu which has a number of features in addition to password management. The only other Vault feature I use is the Payments feature, although I could probably make good use of others.
My personal favorite, although it is not the most important from a security standpoint, is the autofilling of forms. I have to fill out a lot of forms because I often ask for information from websites. It’s so annoying to fill out a several-item form and try to submit it, only to discover that I have to go back and correct a typo. So the password manager makes my online life faster and more convenient and I love it for that. However, auto-fill is not an unmixed blessing: more about that in the Drawbacks section a little further on.
My second favorite thing is that the password manager can store credit card numbers and fetch numbers and billing info while the user is filling out an order. The password manager requires the master password in order to access a credit card, even though the user has already signed in, adding an extra level of security. It also adds to the ease of making purchases online, so you want to watch out for that! I try to be even safer by storing only one credit card online, that one being the one I use for everyday online purchases. Because I use it so much that credit card gets hacked from time to time and the bank immediately and graciously cancels it and issues a new one. That means the credit card in my password manager gets changed more frequently than my other credit cards and that’s good.
Most password managers offer free trial and the user should take advantage of it before deciding. Full-featured password managers are not free and their prices and scope of coverage (mostly additional devices) vary greatly, so be sure to comparison shop. I'm going to do a post on searching soon which will help a lot of people make online comparisons among different products.
The Security section also has useful information. The mobile capture shows an alert I received recently with the company name blacked out since I don't know the status. I immediately changed my password, using the Password Changer feature seen on the menu screen above. It gives strong passwords like bu9zibGWTCuc with a single command. All sites with sensitive data should use a strong, unhackable password like this and with the password manager a user doesn't have to make it up or remember it.

The Password Health screen again shows I don't really pay enough attention. Most of the passwords shown are not the result of a site that has been hacked, although some of them are. They are the result of using the same password as a site that has been hacked. That makes those passwords indirectly unsafe, I think. What I should do is first go through and delete the sites I never use and then change the passwords on the remaining sites. At the very least I should go through the list and see if there are any sensitive sites, primarily those with financial data, listed.
That suggests two more recommendations. First, be selective in setting up accounts on sites. If you do, give no more information than absolutely necessary. The best advice about storing credit card data is just don't do it. If your email address is taken in a hack, that's one thing. If your credit card is stolen, that's a big problem!
Second, think of your password manager account as a closet that needs to be kept clean. If you are prompted to save a password, be sure it is a new one. Otherwise you wind up with a dozen listings for the same account. There will inevitably be a few dups that should be removed manually to ensure that the right password is being fetched.
Possible Drawbacks of Password Managers
Like any other online operation, it is possible for password manager companies to be hacked. Security teams search the web for soft spots and all the major password managers have been called out at one time or another for a vulnerability that could open the door for hackers. These announcements are made public and the password manager firms appear to have been quick to work on the the flaws in their software, unlike many of their colleagues in other lines of work. Security experts themselves use password managers and point out that the benefits of using a password manager outweigh the risks.
Auto-filling is one of those risks. The process allows some hacking routines to syphon off email addresses. If you use it, as I do, be selective. As with everything else about this subject, the better protected the site itself is (a bank, for instance) the safer your data will be. If the site is questionable, the security of your data will be also.
A Final Piece of Advice
When you decide to try out a password manager be sure it is pinned to your start menu. Then it will be ready when you need to use it--and I think you'll be using it a lot!
Consumer Reports has an open article on password managers that you should read before searching for one.
Stay safe!
Update 8/10/18
I forgot to mention that all the major browsers have a password manager. I checked mine on Firefox (Options => Privacy and Security). It has features like saving passwords and autofill. None of my research sites recommended using the password manager on a browser and some specifically recommended against it. That makes sense to me. Browsers are exposed to a lot of websites and that would increase the chance of picking up malware. Keeping passwords in the "locked vault" of a secure app seems to be better advice.
Monday, August 6, 2018
What is the Deep Web and Why Should Internet Users Care?
It’s possible that many of the people who read this don’t—and shouldn’t—care about the dark web. If a user wants to stay on the surface web where it is relatively safe, that’s actually easy to do. I’ll give the definitions first, so if all you want to do is just read those and understand why it’s hard to stray onto the dark web but we use the deep web all the time, then this will make it easy. My hope is that understanding why an innocent user is highly unlikely to find himself on the dark web will make the reader feel safer. If you want a little more information about what’s on the dark web, from someone who hasn’t explored it herself, then do satisfy your curiosity.
The web is generally stratified into three levels as shown in the graphic. The top two levels are:
The Surface Web. The surface web is the portion of the web that is available to be indexed by search engines. It includes platforms large and small, including this blog, and is easily accessible to the user.
Sources indicate that there are currently about 4.49 billion indexed pages on the web. You often see the estimate that as few as 1% or as many as 5% of the pages on the web are actually indexed. While it’s clear that the surface web is, indeed, only the tip of the iceberg, be careful about placing too much faith in the actual statistics. I’ve done enough research to assure myself that the figures I’m giving are directionally correct, but precision is not possible in an environment that is as large and complex as this one. Not to mention that a large part of it is intentionally hidden
To say that the surface web is relatively safe is not to say that there isn’t a lot of nasty stuff on it. It includes adult-only sites (translate that adult porn), hate-filled sites and others including the infamous Ashley Madison site. If you don’t remember that one from the news, it’s a dating site for married adults (!) that was breached in 2015 exposing hundreds of thousands of user records to public (and spousal) scrutiny. These sites all have one thing in common. The visitor knows what they are when she sees them. Just leave.
There are, however, malicious websites that are not evident by their content. Vanderbilt University’s tech blog gives some common signs:
• No SSL certificate (i.e., no “https://” at the beginning of the URL)
• Strange behavior on a legitimate site
• Unwanted downloads
• Unusual URL
• Security tools warnings
I’ll write a bit more about this later, but the best advice is to be sure your security software is kept up to date. It will block most of the offending sites on the surface web.
The Deep Web. The deep web is the part of the internet that’s hidden from search engines. The deep web is huge; perhaps 400 to 500 times the size of the surface web. Again, that's a figure you see often.
The deep web consists of content that is intentionally hidden. That includes things like our social media profiles, employee websites, email--anything that requires a password for access. That means that most of the content on the deep web is innocuous. It's just things we want to keep private.
But if there is nasty stuff on the surface web there is even more, nastier stuff on the dark web. I looked to see if there was a link I could share to give readers as idea, but it was all so gross I have no desire to share it. It is, unfortunately, easily found by searching.
The Dark Web. The dark web is the portion of the deep web where the bad guys hang out. Sites on
the dark web are encrypted and cannot be accessed by search
engines. They can be recognized by an onion symbol similar to the one in this graphic and/or to .onion in the URL.
A special browser is required to access the dark web. The Tor browser is the most famous. The browser itself is not dangerous. It was initially funded by the US government and is used by people like whistle blowers to mask their identities. The dark web is however, full of stolen passwords and illegal drugs. It is also said to be full of malware that will follow a visitor back to his normal haunts.
I have scoured the web to make sure these definitions are correct, and they are. What I have found in the process is that many people who, according to their credentials, should know better are careless. Beware!
We use the deep web all the time, and it is not a problem; it’s where stuff is that we want and need to keep protected. We should care about the dark web, although, since everything is encrypted, it is pretty difficult to stumble onto it. People who are interested in exploring it should listen to a strong warning about the potential dangers, especially malware, of intentionally venturing onto the dark web.
There's an interesting and useful way to demonstrate what can go on there and still stay safe. This site lets the user look to see if her passwords are for sale on the dark web. The word pwned means to absolutely annihilate, as to destroy an opponent in a video game.
I've searched the site occasionally over the past year or so and see passwords from three sites that were hacked some time ago. I'm not exactly sure how to interpret that, although I have been more careful lately. And yes, I have changed the stolen passwords. It’s a site worth bookmarking, although it may restrict frequent use; I can’t tell for sure.
If you stumble onto a site that doesn’t feel right, leave right away and for goodness sake, don’t click anything. But remember that sites that look ok on the surface can be problematic.
I got fooled once by a Dell spoofing site. I was trying to get to Dell support and I kept getting offers for software I didn’t want to buy. I was so naïve that I thought something was wrong with my computer. I took it to Staples where one of the nice tech associates pointed to the URL. It had something before dell in the URL (xxxx.dell.com) and the site had done fancy SEO (search engine optimization) to get it to show up first in Google search. Always look at the URL to see if it looks funny, based on the Vanderbilt criteria above.
And be sure to keep your security software up to date. I just checked mine to be sure. (You should be able to find in in the icons on the bottom right of the screen. If you don’t see it, look in the programs listing.) I checked for updates and found that (1) there were no updates pending and (2) that I have automatic updates on. Be sure yours are on too!
That’s the best single way to stay safe!
Additional Reading
A weird but totally avoidable aspect of the dark web
What is the Deep Web?
The web is generally stratified into three levels as shown in the graphic. The top two levels are:
 |
Sources indicate that there are currently about 4.49 billion indexed pages on the web. You often see the estimate that as few as 1% or as many as 5% of the pages on the web are actually indexed. While it’s clear that the surface web is, indeed, only the tip of the iceberg, be careful about placing too much faith in the actual statistics. I’ve done enough research to assure myself that the figures I’m giving are directionally correct, but precision is not possible in an environment that is as large and complex as this one. Not to mention that a large part of it is intentionally hidden
To say that the surface web is relatively safe is not to say that there isn’t a lot of nasty stuff on it. It includes adult-only sites (translate that adult porn), hate-filled sites and others including the infamous Ashley Madison site. If you don’t remember that one from the news, it’s a dating site for married adults (!) that was breached in 2015 exposing hundreds of thousands of user records to public (and spousal) scrutiny. These sites all have one thing in common. The visitor knows what they are when she sees them. Just leave.
There are, however, malicious websites that are not evident by their content. Vanderbilt University’s tech blog gives some common signs:
• No SSL certificate (i.e., no “https://” at the beginning of the URL)
• Strange behavior on a legitimate site
• Unwanted downloads
• Unusual URL
• Security tools warnings
I’ll write a bit more about this later, but the best advice is to be sure your security software is kept up to date. It will block most of the offending sites on the surface web.
The Deep Web. The deep web is the part of the internet that’s hidden from search engines. The deep web is huge; perhaps 400 to 500 times the size of the surface web. Again, that's a figure you see often.
The deep web consists of content that is intentionally hidden. That includes things like our social media profiles, employee websites, email--anything that requires a password for access. That means that most of the content on the deep web is innocuous. It's just things we want to keep private.
But if there is nasty stuff on the surface web there is even more, nastier stuff on the dark web. I looked to see if there was a link I could share to give readers as idea, but it was all so gross I have no desire to share it. It is, unfortunately, easily found by searching.
How is the Dark Web Different from the Deep Web?
The Dark Web. The dark web is the portion of the deep web where the bad guys hang out. Sites on
the dark web are encrypted and cannot be accessed by search
engines. They can be recognized by an onion symbol similar to the one in this graphic and/or to .onion in the URL.
A special browser is required to access the dark web. The Tor browser is the most famous. The browser itself is not dangerous. It was initially funded by the US government and is used by people like whistle blowers to mask their identities. The dark web is however, full of stolen passwords and illegal drugs. It is also said to be full of malware that will follow a visitor back to his normal haunts.
I have scoured the web to make sure these definitions are correct, and they are. What I have found in the process is that many people who, according to their credentials, should know better are careless. Beware!
Should Users Care About the Deep Web and the Dark Web?
We use the deep web all the time, and it is not a problem; it’s where stuff is that we want and need to keep protected. We should care about the dark web, although, since everything is encrypted, it is pretty difficult to stumble onto it. People who are interested in exploring it should listen to a strong warning about the potential dangers, especially malware, of intentionally venturing onto the dark web.
There's an interesting and useful way to demonstrate what can go on there and still stay safe. This site lets the user look to see if her passwords are for sale on the dark web. The word pwned means to absolutely annihilate, as to destroy an opponent in a video game.
I've searched the site occasionally over the past year or so and see passwords from three sites that were hacked some time ago. I'm not exactly sure how to interpret that, although I have been more careful lately. And yes, I have changed the stolen passwords. It’s a site worth bookmarking, although it may restrict frequent use; I can’t tell for sure.
The Take-Aways
If you stumble onto a site that doesn’t feel right, leave right away and for goodness sake, don’t click anything. But remember that sites that look ok on the surface can be problematic.
I got fooled once by a Dell spoofing site. I was trying to get to Dell support and I kept getting offers for software I didn’t want to buy. I was so naïve that I thought something was wrong with my computer. I took it to Staples where one of the nice tech associates pointed to the URL. It had something before dell in the URL (xxxx.dell.com) and the site had done fancy SEO (search engine optimization) to get it to show up first in Google search. Always look at the URL to see if it looks funny, based on the Vanderbilt criteria above.
And be sure to keep your security software up to date. I just checked mine to be sure. (You should be able to find in in the icons on the bottom right of the screen. If you don’t see it, look in the programs listing.) I checked for updates and found that (1) there were no updates pending and (2) that I have automatic updates on. Be sure yours are on too!
That’s the best single way to stay safe!
Additional Reading
A weird but totally avoidable aspect of the dark web
Subscribe to:
Posts (Atom)
Why I'm Writing A Blog About Personal Data Protection
The subhead states the mission of the blog. I want to make key methods for protecting user data privacy and identify comprehensible to the m...
-
Data privacy issues are global because the internet itself is global. Actually, it's becoming less so as China builds its own version an...
-
The subhead states the mission of the blog. I want to make key methods for protecting user data privacy and identify comprehensible to the m...
-
The blog Phishing.org defines phishing as a cybercrime in which a target or targets are contacted by email, telephone or text messag...